Blog
The Dilemma of Defense in Depth
By Ala’ F. Wrikat, MSc, CISSP, CISM. Ala’ is currently a specialist in policies and strategic studies at the Financial-sector’s CERT of Jordan.
Defense in depth strategy has proven its effectiveness in preventing cyber threats over the years. At the abstract level, most technical security controls are designed with two main components; 1) a knowledge base, and 2) a matching engine. Each security product has its own version of a growing knowledge base of feeds (whatever these feeds are). The content and how frequent these knowledge bases get updated are often the basis of competition between vendors. In this context, where these knowledge bases are complementary, defense in depth is meaningful.
However, with the emergence of Artificial Intelligence (AI) and Machine Learning (ML)-driven security controls, traditional defense in depth strategies are not as valid as they used to be.
To justify this claim, we consider the serial setup shown in the figure below. At the leftmost, two controls, A and B, are implemented as expert systems with real-time response capabilities. They are situated serially to protect some assets from adverse transactions sourcing from an unknown network.
In scenario 1, a truly malign transaction was falsely labeled as benign at control A, and was allowed to pass-through. However, control B, was able to correctly spot and prevented it from proceeding further. In this case, control A, had no idea that a false negative has just been committed by it. Thus, leading to a case of growing fallacies at control A.
In scenario 2, if the malign transaction is correctly flagged and dropped at Control A, a case of limited knowledge happens at control B.
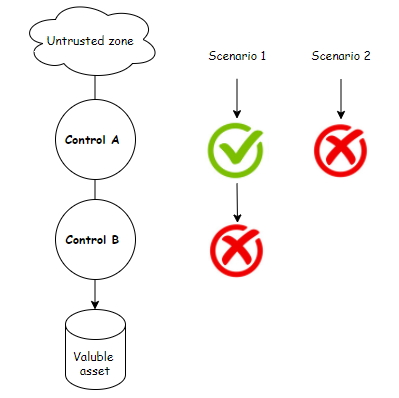
In the context of machine learning, In-series controls are not complementary and traditional defense in depth is meaningless. The resultant limited and falsified knowledge hamper the predictive power of machine learning capabilities.
Defense strategies need to keep pace with technological advancement in technical measures. Innovations and research efforts should start looking into ways to break down the silos between distinct security controls and maximize the utilization of cyber defense investments.
